2 minutes
SSH Tunneling over SSM Session Manager
During my day job, I was assisting a developer remotely develop on an EC2 instance using the VSCode extension “Remote - SSH”. As a Security Engineer™, I would prefer not to open any SSH ports to the internet, or at all, especially since we already have SSM Session Manager setup.
I stumbled upon this article Transparently develop on an EC2 instance with VSCode Remote SSH — through SSM by Dennis Bappert which goes through the steps of setting up SSH over SSM. This made me wonder if you could use the SSH tunnel for a SOCKS proxy, local/remote port forwarding for Post-Exploitation activities.
The answer is yes, and it’s quite simple.
Setup and Pre-Requisites
- SSM Session Manager is setup on the EC2/Account.
- The Session Manager Plugin is setup on your machine.
- SSH keys are setup on the EC2 and your machine. This can be done over an SSM session with
aws ssm start-session. - Your SSH config looks like the SSH config below
Host myec2box
User ssm-user
IdentityFile ~/.ssh/myec2box.id_rsa
ProxyCommand aws ssm start-session --target i-05108aba3d4c4d704 --profile default --region us-east-2 --document-name AWS-StartSSHSession --parameters portNumber=%p
Note: The instace ID will need to be changed to your instance ID.
- Your AWS cli is configured with your target credentials. e.g. ENV vars or IAM User creds.
SOCKS over SSH over SSM
If the setup and pre-requisites are followed, then all you have to do now is do SOCKS (Dynamic Port Forwarding) as normal with SSH client.
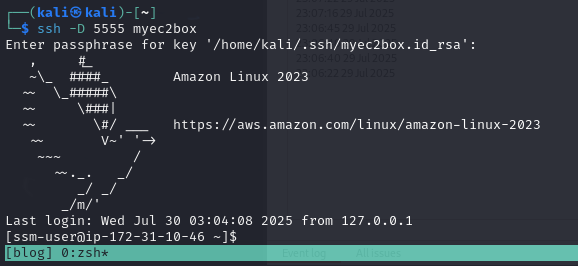
ssh -D 5555 myec2box
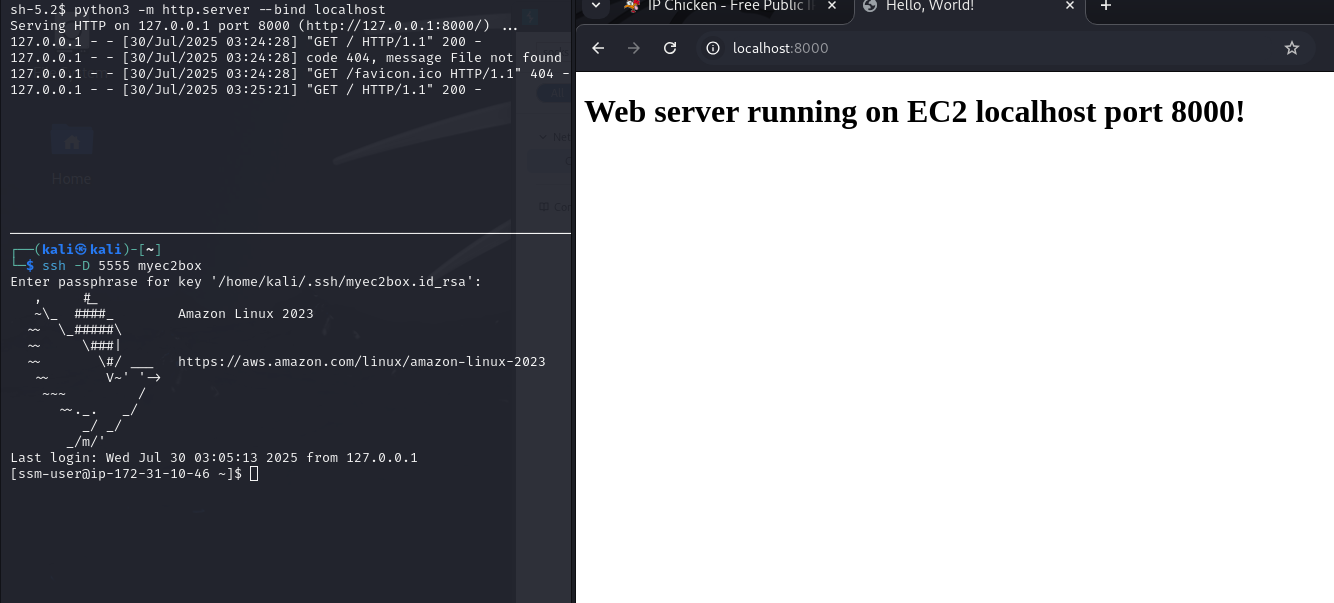
Lastly, connect to the SOCKS proxy on the localhost/port. The example below has Burp Suite configured to use SOCKS proxy to connect to a Python web server running on localhost:8000 on the EC2.
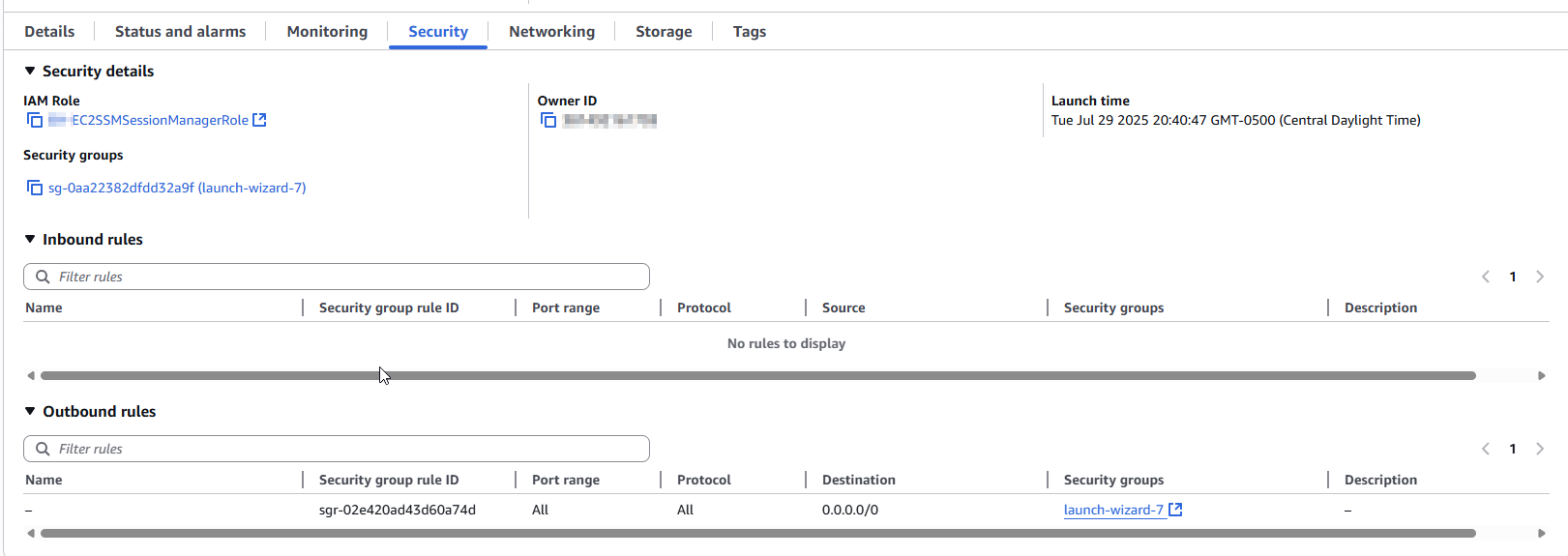
All of this was done without modifying or even having a single Security Group inbound rule.